|
Postfix + Clamav + Amavisd
2017/12/23 |
|
Configure Virus-Scanning with Postfix + Clamav.
|
|
| [1] | |
| [2] | Install Amavisd and Clamav Server, and start Clamav Server first. |
|
[root@mail ~]#
[root@mail ~]# dnf -y install amavisd-new clamav-server clamav-server-systemd cp /usr/share/doc/clamav-server*/clamd.sysconfig /etc/sysconfig/clamd.amavisd
[root@mail ~]#
vi /etc/sysconfig/clamd.amavisd # line 1,2: uncomment and change CLAMD_CONFIGFILE=/etc/clamd.d/ amavisd.conf CLAMD_SOCKET=/var/run/ clamd.amavisd /clamd.sock
[root@mail ~]#
vi /etc/tmpfiles.d/clamd.amavisd.conf # create new d /var/run/clamd.amavisd 0755 amavis amavis -
[root@mail ~]#
vi /usr/lib/systemd/system/clamd@.service # add follows to the end [Install] WantedBy=multi-user.target systemctl start clamd@amavisd [root@mail ~]# systemctl enable clamd@amavisd |
| [3] | If SELinux is enabled, add rules like follows. |
|
[root@mail ~]#
dnf -y install checkpolicy policycoreutils-python-utils
[root@mail ~]#
setsebool -P antivirus_can_scan_system on [root@mail ~]# setsebool -P antivirus_use_jit on [root@mail ~]# vi amavisd.te # create new
module amavisd 1.0;
require {
type antivirus_t;
type antivirus_exec_t;
type antivirus_db_t;
type antivirus_var_run_t;
type init_t;
type razor_port_t;
type amavisd_send_port_t;
type tmpreaper_exec_t;
class file { append create getattr execute_no_trans ioctl link open read rename setattr unlink write lock map };
class dir { add_name create read remove_name setattr write rmdir };
class tcp_socket name_connect;
class sock_file write;
class process execmem;
class unix_stream_socket connectto;
}
#============= init_t ==============
allow init_t antivirus_t:unix_stream_socket connectto;
allow init_t antivirus_exec_t:file { execute_no_trans ioctl };
allow init_t amavisd_send_port_t:tcp_socket name_connect;
allow init_t antivirus_db_t:dir { add_name create read remove_name setattr write rmdir };
allow init_t antivirus_db_t:file { append create getattr ioctl link open read rename setattr unlink write lock };
allow init_t antivirus_var_run_t:file { create write };
allow init_t antivirus_var_run_t:sock_file write;
allow init_t razor_port_t:tcp_socket name_connect;
allow init_t tmpreaper_exec_t:file execute_no_trans;
allow init_t self:process execmem;
allow antivirus_t antivirus_db_t:file map;
checkmodule -m -M -o amavisd.mod amavisd.te checkmodule: loading policy configuration from amavisd.te checkmodule: policy configuration loaded checkmodule: writing binary representation (version 17) to amavisd.te [root@mail ~]# semodule_package --outfile amavisd.pp --module amavisd.mod [root@mail ~]# semodule -i amavisd.pp |
| [4] | Configure Amavisd. |
|
[root@mail ~]#
vi /etc/amavisd/amavisd.conf # line 20: change to the own domain name $mydomain = ' srv.world ';
# line 152: change to the own hostname $myhostname = ' mail.srv.world ';
# line 154: uncomment $notify_method = 'smtp:[127.0.0.1]:10025'; $forward_method = 'smtp:[127.0.0.1]:10025'; systemctl start amavisd spamassassin [root@mail ~]# systemctl enable amavisd spamassassin |
| [5] | Configure Postfix. |
|
[root@mail ~]#
vi /etc/postfix/main.cf # add follows to the end content_filter=smtp-amavis:[127.0.0.1]:10024
[root@mail ~]#
vi /etc/postfix/master.cf # add follows to the end
smtp-amavis unix - - n - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
127.0.0.1:10025 inet n - n - - smtpd
-o content_filter=
-o local_recipient_maps=
-o relay_recipient_maps=
-o smtpd_restriction_classes=
-o smtpd_client_restrictions=
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o mynetworks=127.0.0.0/8
-o strict_rfc821_envelopes=yes
-o smtpd_error_sleep_time=0
-o smtpd_soft_error_limit=1001
-o smtpd_hard_error_limit=1000
systemctl restart postfix |
| [6] | It' OK all. [X-Virus-Scanned: ***] lines are added in the header section of emails after this configuration and emails with known Virus will not sent to Clients. |
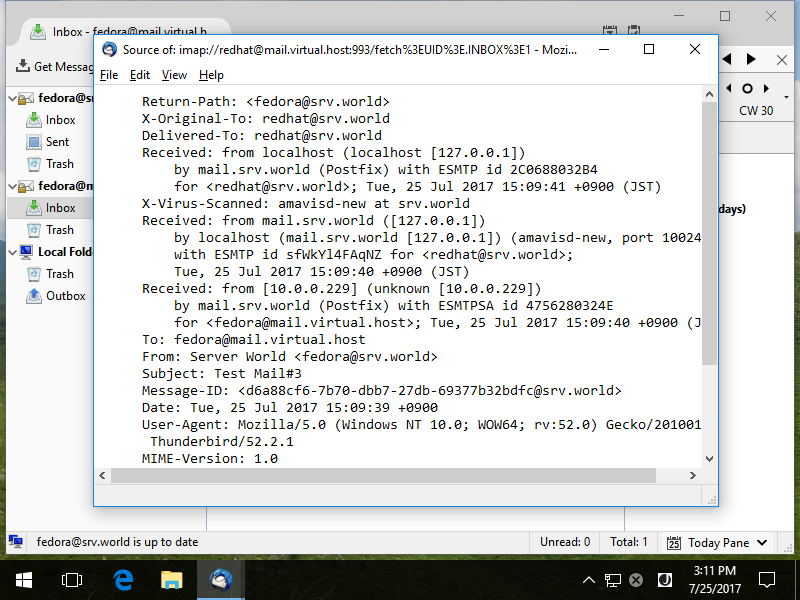
|